Security-Management (ISMS)
The application for documentation, control and evaluation of information security
We are here for you.
Arrange a personal and unbinding demo appointment now.
Comprehensive assessment and management of information security
Security in information and data management is one of the most delicate tasks in a company. In addition to the pure data protection, the topic gets more and more attention and dynamics through hacker attacks. This attention is also justified, since information is one of the most important assets of a company. Be it strategies, patents, information about customers, suppliers, products as well as information about ongoing business and transformation projects. Other essential and sensitive information includes existing or planned resources as well as information on risks, controls or gaps in the implementation of regulatory requirements.


How TopEase® supports you:
TopEase® has comprehensive, integrated, and sustainable security management that does not require redundancy. All safety regulations and standards are supported by TopEase®.
Especially worth mentioning are the BSI specifications and the standards 27001 et seq. TopEase® also allows permanent evaluation of information security and the monitoring of recommendations, weaknesses and measures.
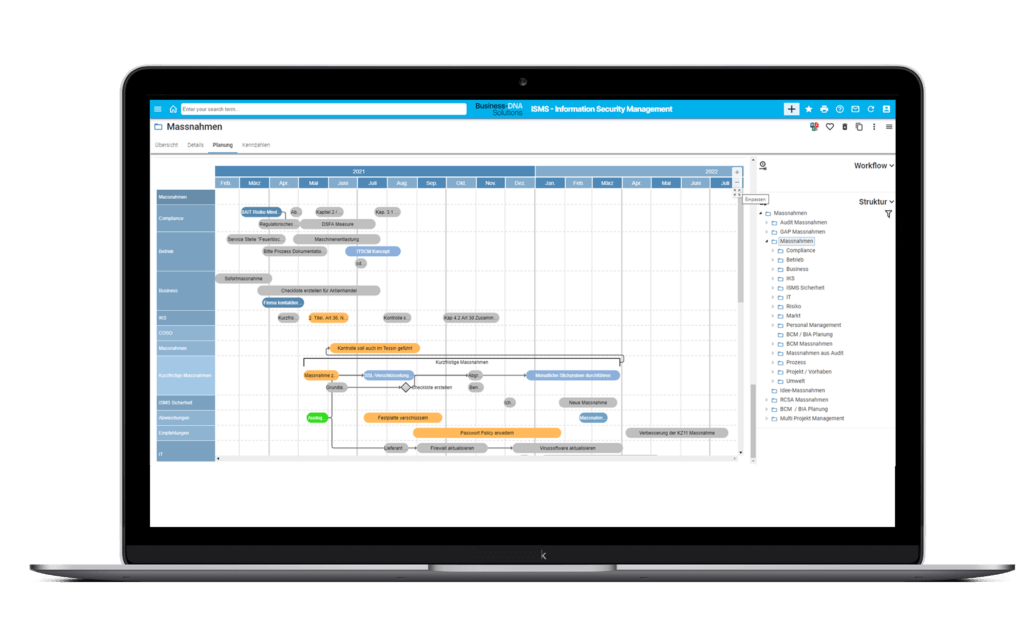
Security Assessment and Management Solution
Asset overview

Your advantages with TopEase®
- Security specifications can be documented, maintained, evaluated, measured, controlled and changed comprehensively and redundantly.
- Integration with risk, process & control management is comprehensively guaranteed.
- Security specifications can be linked to all assets (processes, organisational units, systems, applications, infrastructure, logistics, equipment,contracts, suppliers, etc.).
- Comprehensive definition of governance for risks, controls and security requirements.
- Overall care and evaluation of protection needs.
- Protection needs analysis forms the basis for the entire ISM process.
- Automatic determination of all bases to be assessed in the process on the basis of a scope (value added / process)

Meets regulatory
requirements
Modular & mobile

Importing own data possible
OnPremise or SaaS

Swiss-Made
We are here for you.
We are happy to answer your questions about TopEase®.
Questions about the TopEase® features?
Telephone
+44 1923 437 784
80%
savings due to automatically generated graphics and documents.
30-50%
increase in productivity.